Analyzing resources consumed in a Slowloris Attack
Overview
This exercise will demonstrate Slowloris attack and analyze the resources it consumes.
Required Reading
Introduction
A Slowloris attack is an application-layer attack, which operates by utilizing partial HTTP requests. The attack functions by opening connections to a targeted Web server and then keeping those connections open as long as it can.
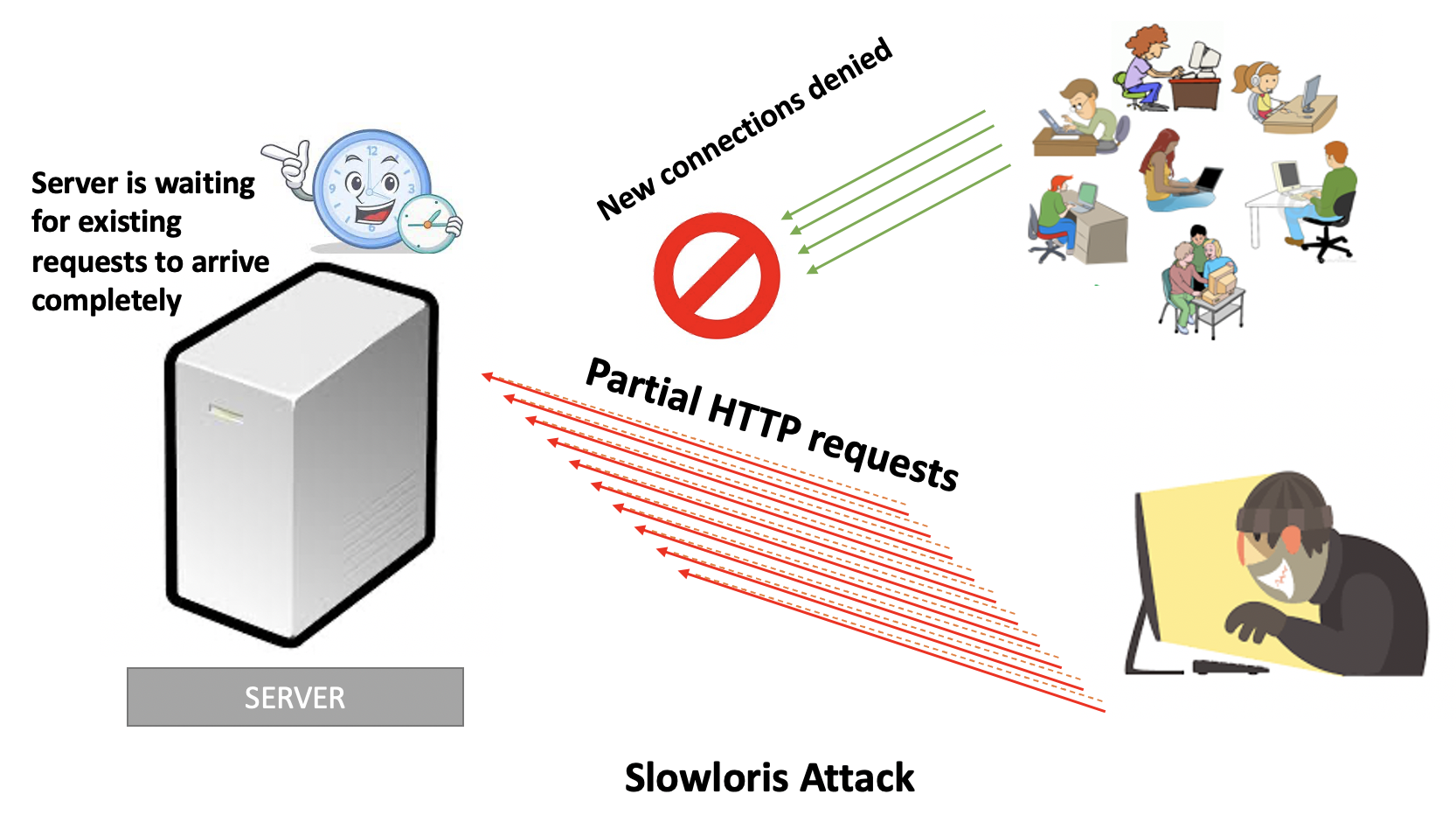
Slowloris keeps connections open by continuously sending partial Web requests. Since the request is never completed the server cannot process it and close the connection. Affected servers will keep these connections open, filling their maximum concurrent connection pool, eventually denying additional connection attempts from legitimate clients.
Attack Tool
You can find the Slowloris attack tool on the attacker node in /tmp/attacker/slowloris folder. The tool was cloned from https://github.com/gkbrk/slowloris.
Assignment Instructions
Setup
Tasks
Server installation and measurement
On the server node, install apache2 and tune tcp parameters. You can use the following commands:
sudo apt-get update
sudo apt-get install apache2
sudo sysctl -w net.ipv4.tcp_syn_retries=1
sudo sysctl -w net.ipv4.tcp_max_syn_backlog=10000
Legitimate traffic
Write a simple script to generate legitimate traffic from the client node. You can generate 50 legitimate requests per second by giving a sleep of 0.02 seconds. To prevent legitimate requests from flooding the server, you can timeout requests after 10 seconds if a legitimate connection can't be established with the server in 10 seconds. You can use wget or curl in your script. Example usage:wget server --connect-timeout=10 or curl server --connect-timeout=10
Next, start collecting tcpdump on the server node. tcpdump is the most powerful and widely used command-line packets sniffer or packet analyzer tool, which is used to capture TCP/IP packets that are received or transferred over a network on a specific interface. We capture packets in this exercise, so that we can measure the time taken by each connection.
For a closer look into resource consumption, write a script to probe the output of netstat command every second. This will help you measure the number of open sockets, connections and their current states.
Scenario
- Start measuring with tcpdump and netstat
- Start the legitimate client script
- Wait about 60 seconds
- On attacker node, start the attack by running the commands:
cd /tmp/attacker/slowloris python3 slowloris.py server -s 3500 --sleeptime 0 - Let the attack run for 2 minutes
- Stop both the legitimate and attack traffic. Stop collecting tcpdump on the server. Kill the netstat script on the server.
Calculating statistics
Using the output of tcpdump, calculate connection durations for all successful connections.The connection duration of a successful connection is the time elapsed between the server receiving the first SYN packet and the last FIN on the connection. Measure the durations for all legitimate connections and attack connections separately.
Also, measure the number of unsuccessful connections per second -- these connections just have repeating SYN packets. Plot the number of successful attack and legitimate connections, and the number of unsuccessful attack and legitime connections per second in a graph.
Use the output of the netstat script to find the number of sockets per second that are in SYN_RECV state. SYN_RECV denotes that a connection request has been received from the network but the connection has not yet progressed to ESTABLISHED state.
Submission Instructions
Submit a Word document with the following items (label each section):- Explain how the Slowloris attack works.
- Discuss what could be a defense for the Slowloris Attack?
- Include your legitimate client script.
- Specify the tcpdump command that you used for capturing the packets.
- Include the netstat script that you wrote.
- Using your statistics, draw a graph showing the number of successful and unsuccessful legitimate and attack connections. What can you infer from this graph?
- Specify average legitimate connection duration for successful attack and legitimate connections.
- What is the average number of sockets per second, associated with legitimate traffic, that remains in SYN_RECV state: (a) before the attack, and (b) during the attack?
 .
.